Security¶
A few points about our security practices:
- All solutions are built referencing best practices such as “The Twelve-Factor” and the various OWASP guidelines (i, ii)
- We host only with the leading IaaS providers that are all GDPR compliant (available on request)
- We use the best and latest technologies available for the web
- We use 4096 bit SSH keys for server access
- We only use encrypted tunnels for resource access
- Our databases are hosted by Compose.io (an IBM company) or mLab (MongoDB) and run sharded and/or in replica sets for performance & HA
- Our whole application stack is fronted by Cloudflare which provides us
- Internet security
- DDOS detection & prevention
- Realtime DNS management
- Load balacing
- Network performance monitoring & routing
- CDN
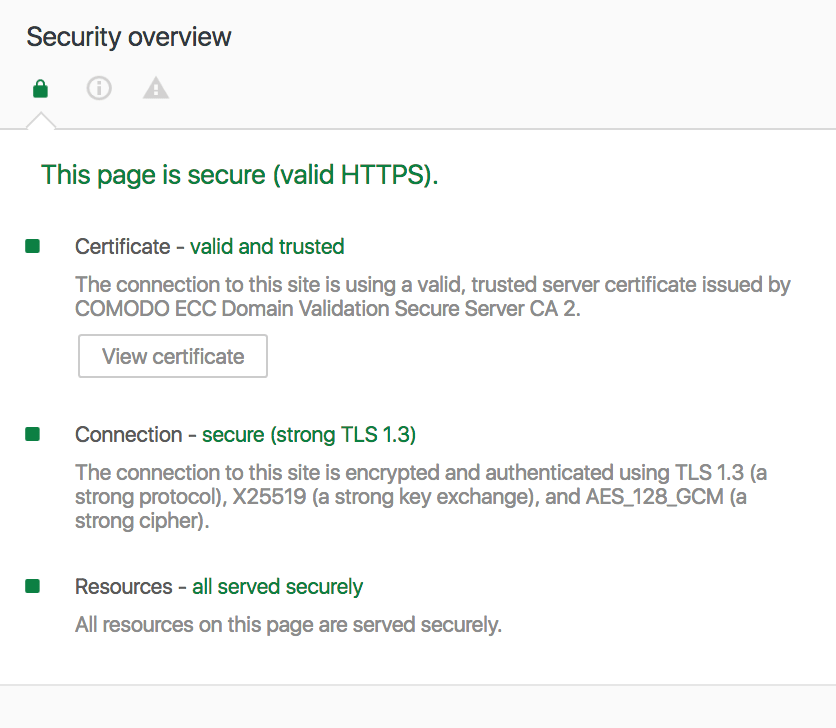
- And is served using TLS 1.3/HTTP2 and the best HTTPS/SSL encryption technologies where possible (ECC)
- In the system we have role based authorization per invidual company, and we focus on security front-to-back
A brief HTTPS overview below: